2 Computer Hardware, Software, and Networks
Learning Objectives
- Define information technology.
- Identify the components of information technology.
- Describe operating systems.
- Understand database management systems.
- Recognize the difference between the internet, intranet, and extranet.
Introduction
Computer hardware refers to the physical components of a computer system, including the central processing unit (CPU), motherboard, memory, hard drive, graphics card, sound card, and other peripherals such as a keyboard, mouse, and monitor. These components work together to allow a computer system to perform tasks and run programs. A computer can be a desktop, laptop, tablet, or smartphone, and is usually connected to the internet, allowing for access to a wide range of software applications and online resources.
How do Computers Work?
At a basic level, a computer works through a series of interconnected hardware and software components, each designed to perform specific functions. When a user inputs a command, such as typing on a keyboard, the computer receives the input and processes it through the Central Processing Unit, or CPU, which acts as the brain of the computer. The CPU fetches instructions from memory and executes them, performing calculations and logical operations at incredibly high speeds.
The computer’s Random Access Memory, or RAM, acts as a temporary storage space for data, holding information that is being actively used by the CPU. Meanwhile, the hard drive or solid-state drive (SSD) stores data and programs for long-term use. When the user opens a program or file, the computer retrieves the necessary data from the hard drive and loads it into RAM for processing.
The computer’s input/output devices, such as the keyboard, mouse, and monitor, allow users to interact with the computer and receive feedback on its operations. For example, when a user clicks on an icon with a mouse, the computer registers the input and performs the corresponding action, displaying the results on the monitor.
To summarize, the complex interplay of hardware and software components enables a computer to perform a vast array of tasks, from basic word processing to complex scientific simulations. As technology continues to advance, computers are becoming ever more powerful and versatile, and their capabilities are limited only by the imagination of their users.
Binary – the mathematical language of computers
The binary system is a way of representing information in a computer using only two digits, 0 and 1. This is because computers are electronic devices and use electricity to process and store information, which can either be present (represented by 1) or absent (represented by 0). This is called a binary digit or bit. Computers use the binary system to work by interpreting binary code, which is a series of 0s and 1s that represent different commands and data.
Using only 0s and 1s, all kinds of information can be represented, from numbers and letters, to photographs and audio files. For example, the binary code 01100100 represents the letter “d” in ASCII encoding. To perform binary math, a computer uses tiny electronic circuits called logic gates to perform basic mathematical operations such as addition, subtraction, multiplication, and division. For instance, to add two binary numbers, the computer uses a circuit called a full adder, which takes in two binary inputs and returns a binary output representing the sum of the two numbers.
For example, to add the binary numbers 1011 (eleven in decimal) and 1101 (13 in decimal), the computer would start from the rightmost digit and add each pair of digits.
1 0 1 1 (11)
+ 1 1 0 1 (13)
1 1 0 0 0 (24)
Digital Measures
Digital bits are usually combined into groups of eight bits to form a byte. Bytes are sufficiently large to store characters and numbers. Computer memory and storage devices are measured in powers of two. A megabyte, abbreviated MB, is 210 or 1,024 bytes. A gigabyte is 1,024 megabytes, and so on (see table below) for some comparisons.
| Unit | Number of Bytes | Storage Examples |
| kilobyte | 1,024 | 2-3 paragraphs of text |
| megabyte | 1,048,576 | Text of a 1 book |
| gigabyte | 1,073,741,824 | Text of about 4,500 books |
| terabyte | 1,099,511,627,776 | Text of 4.5 million books |
| petabyte | 1,125,899,906,842,624 | Text of 4.7 billion books |
Hardware Components of a Computer
Central Processing Unit (CPU)
The CPU, or central processing unit, is the primary component of a computer’s hardware that performs most of its processing tasks. It is essentially the brain of the computer and controls all of its functions. The CPU performs calculations, logical operations, and manages data flow between other parts of the computer, such as RAM and the hard drive. It executes instructions stored in memory and runs software programs, which allows the computer to perform specific tasks such as word processing, gaming, and browsing the internet. The speed and efficiency of a CPU determine how fast a computer can perform tasks and run applications. Higher-end CPUs are typically faster and more powerful, allowing for faster processing speeds and better performance.
Logic Gates
Logic gates are electronic circuits that perform logical operations, such as AND, OR, NOT, and XOR, on binary inputs. These operations are based on Boolean algebra, a branch of mathematics that deals with binary logic. Each logic gate has one or more inputs and one output, that depends on the logic of the inputs.
In a CPU, logic gates are incorporated into the arithmetic logic unit (ALU), which is responsible for performing mathematical and logical operations on data. The ALU contains many logic gates, as well as other circuits and registers that allow it to perform a wide range of operations.
Graphics Processing Unit (GPU)
A GPU, or graphics processing unit, is a specialized type of processor designed for handling graphical and visual data. GPUs are particularly important for gaming, video editing, and other applications that require high-quality graphics and fast processing speeds. A GPU works by offloading some of the processing tasks that would normally be handled by the CPU, allowing for more efficient and faster performance.
When a computer runs a graphics-intensive application, such as a video game or 3D rendering software, the GPU takes over much of the processing load, freeing up the CPU to handle other tasks. GPUs are optimized for performing calculations related to graphics and visual data, which allows them to process large amounts of data quickly and efficiently. They are typically more powerful than the integrated graphics processors found in most CPUs and are often used in desktop computers and high-end laptops.
Gordon Moore and Moore’s Law
Gordon Moore is a renowned American engineer and entrepreneur who co-founded Intel Corporation in 1968. Under Moore’s leadership, Intel became the world’s largest supplier of microprocessors, and his contributions to the development of the semiconductor industry have been recognized with numerous honors and awards. He is perhaps best known, however for Moore’s Law, which predicted a revolution in the world of computing.
In 1965, Moore observed that the number of transistors on a microchip was doubling every two years, resulting in an exponential increase in computing power while simultaneously reducing cost and size. This observation became known as Moore’s Law and has become the predictive force behind the development of modern computing technology.
Moore’s Law has withstood the test of time, with the number of transistors on a microchip continuing to double every two years until recently. Although the physical limits of transistor size present a challenge to the future of Moore’s Law, the trend has already had a profound impact on computing and technology. 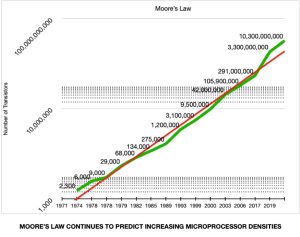
Motherboard
A computer motherboard, also known as a mainboard, is a flat board that connects all the components of the computer, including the CPU, RAM, storage devices, expansion cards, and other peripherals.

Its purpose is to provide a communication pathway and physical connection between different computer parts. It is essentially the backbone of the computer system, serving as the central hub to which all other parts of the computer connect.
The motherboard also houses the BIOS or UEFI firmware that allows the computer to boot up and run its essential software. BIOS (Basic Input/Output System) or UEFI (Unified Extensible Firmware Interface) firmware is the software that is built into the motherboard of a computer. It is responsible for controlling the fundamental hardware operations of the system, such as booting up the computer and managing the communication between the operating system and the hardware.
What is unique about firmware is that it is stored in non-volatile memory, usually in a ROM or flash memory chip, and is not erased when the computer is turned off. This means that the firmware remains intact even if there is a power outage or if the computer is reset. Firmware can be updated or flashed to make changes to the way a computer operates. It is also unique in that it is specific to the hardware it is controlling, meaning that firmware for one computer may not be compatible with another.
In summary, the motherboard is an essential part of a computer, and without it, a computer cannot function.
Memory – RAM and ROM
RAM, or random access memory, is a type of computer memory that is used to temporarily store data and program instructions that are currently in use by the computer’s CPU. RAM is volatile, meaning that it requires power to maintain its contents, and is cleared when the computer is turned off. RAM is important for computer performance because it provides fast access to data and program instructions, allowing the CPU to work efficiently.
ROM, or read-only memory, is a type of computer memory that is used to store permanent data and program instructions that are essential to the computer’s operation, such as the BIOS or UEFI firmware. ROM is non-volatile, meaning that it does not require power to maintain its contents, and is not erased when the computer is turned off. ROM is important for computer operation because it provides essential instructions and data that the computer needs to function properly.
RAM and ROM are both used in a computer to store and access data and program instructions. RAM is used to temporarily store data while the computer is running, while ROM is used to store permanent data and program instructions that are necessary for the computer to function. Together, RAM and ROM provide a complete memory system for a computer, allowing it to perform a wide range of tasks and run a variety of software applications.
Data Storage
Data on a computer can be stored in various ways, such as on hard drives, solid-state drives (SSD), and removable media like USB flash drives or CDs/DVDs.
 Hard drives are mechanical storage devices that use spinning disks to read and write data, with the data being accessed by magnetic read/write heads. Hard drives store data even when a computer is turned off and typically have a larger storage capacity than SSDs, making them ideal for storing large amounts of data.
Hard drives are mechanical storage devices that use spinning disks to read and write data, with the data being accessed by magnetic read/write heads. Hard drives store data even when a computer is turned off and typically have a larger storage capacity than SSDs, making them ideal for storing large amounts of data.
Solid-state drives (SSD) use electronic circuits to store data instead of mechanical spinning disks. They are faster than hard drives because there are no moving parts that need to be accessed. Their storage capacity is generally smaller compared to hard drives. They are ideal for use as the primary or boot drive because they offer faster boot times and faster application load times, making them ideal for people who need the speed more than large storage capacity.
Removable media like USB flash drives, CDs/DVDs and memory cards are used for storing and sharing data, especially when portability is needed. They can be inserted into a USB or memory card port on a computer or mobile device, and data can be added, deleted, or modified as needed. They are not ideal for use as a primary storage device, but they’re a great way to back up or transfer data between computers or as temporary storage to free up computer memory.
Input and Output
Computer input devices are tools that allow users to interact with a computer system. They are used to transmit signals and data into the computer itself, facilitating communication between man and machine. Here are some examples of input devices:
Keyboard: A keyboard is a common input device that is used to enter characters, numbers, and other text into a computer. Almost all PCs and laptops come with an integrated keyboard. 
Mouse: A mouse is another popular input device that is used to control the movement of a cursor on a screen. It allows the user to select and click on items on the screen.
Scanner: A scanner is a device that captures images or text from printed documents and converts them into a digital format that can be displayed on a computer screen.
Microphone: A microphone allows the user to input audio data into a computer. It is commonly used for recording voiceovers, podcasts, and other types of audio content.
Computer output devices take digital data from a computer system and present it to the user in various forms, such as sound, text, images, or video. Here are some examples of output devices:
Monitor: A monitor is a common output device that displays visual data that a computer is processing. It can be a Cathode Ray Tube (CRT), Liquid Crystal Display (LCD), or Light-Emitting Diode (LED) display.
Printer: A printer is an output device that produces a hard copy of a digital file. It can be used to print text or images.
Speaker: A speaker is an output device that converts digital signals into sound. It is used to play music, voice recordings or other audio files.
Projector: A projector is an advanced output device which projects an image or video onto a large screen or wall. It is commonly used in presentations or home theatre systems.
Input and output devices are fundamental to the operation of computer systems. Generically, these are often called peripheral devices because they operate outside the core components of the computer itself. Peripherals are often wired devices that connect to a computer’s Universal Serial Bus (USB), High Definition Multimedia Interface (HDMI), or similar port. Some peripheral devices may use Bluetooth technology to connect peripherals to a computer wirelessly.
Bluetooth allows devices to communicate with each other wirelessly over short distances. It is commonly used for peripherals such as wireless mice, keyboards, and headphones, as well as for file transfers between devices such as smartphones and computers. Bluetooth works by using radio waves to establish a connection between two devices and exchanging data between them. The devices must be within close proximity to each other, usually within a few meters, for the Bluetooth connection to work. This technology provides a convenient and efficient way for users to connect and use peripherals with their computers without the need for cables or wires.
Introduction to Software
Computer software is a collection of programs, data, and instructions that tell a computer what to do. This includes operating systems, applications, utilities, and any other programs that are used on a computer or other electronic device. Software is designed to be interpreted by a machine, and it can be stored and executed on a variety of computing devices, such as desktops, laptops, tablets, smartphones, and servers. The software is responsible for managing hardware resources, performing complex calculations, manipulating data, providing user interfaces, and enabling communication among various components of a system.
Types of Software
Operating Systems
A computer operating system is a collection of software programs that manages computer hardware resources and provides common services for computer programs. Examples of commonly used operating systems include Microsoft Windows, macOS, Linux, and Android.
 We need an operating system because it provides a common interface for users to interact with the computer’s hardware and software. Without an operating system, we would have to interact directly with the computer’s hardware, which would be tedious and difficult. The operating system also manages system resources, such as memory and processing power, to ensure that different programs can run simultaneously without interfering with each other. Additionally, the operating system provides security features to protect against malware and unauthorized access to the system.
We need an operating system because it provides a common interface for users to interact with the computer’s hardware and software. Without an operating system, we would have to interact directly with the computer’s hardware, which would be tedious and difficult. The operating system also manages system resources, such as memory and processing power, to ensure that different programs can run simultaneously without interfering with each other. Additionally, the operating system provides security features to protect against malware and unauthorized access to the system.
How Computers Work: Hardware and Software – YouTube
Application Software
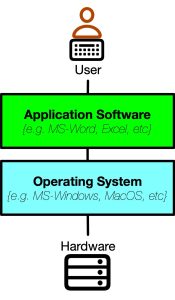
Application software, or “apps,” are programs that are designed to perform specific tasks or functions for users. They are usually developed for a specific platform or operating system, such as Windows, iOS, or Android, and can be downloaded and installed onto a device from an app store or website. Examples of application software include:
Adobe Photoshop: a graphics editing program used for photo manipulation, image enhancement, and graphic design.
Google Chrome: a web browser used for accessing the internet and viewing websites.
Spotify: a music streaming service used for listening to music and creating playlists.
Zoom: a video conferencing program used for online meetings and virtual events.
QuickBooks: an accounting software used for managing finances and bookkeeping for small businesses.
Snapchat: a social media app used for sharing photos and videos with friends.
Uber: a transportation app used for booking rides and getting around in urban areas.
Minecraft: a video game used for building, exploring, and creating virtual worlds.
TikTok: a social media app used for creating and sharing short videos.
Office Software
Office software apps refer to a suite of productivity software programs used for creating and editing documents, spreadsheets, presentations, and email. Examples of office software include Microsoft Office, Google Workspace, LibreOffice, and Apple iWork.
Using office software instead of stand-alone apps allows for more streamlined and efficient workflows, as all the tools needed for productivity work are housed in one platform. This makes it easier to switch between tasks and to collaborate with others on shared documents, spreadsheets, and presentations. Additionally, office software often provides more advanced features and customization options, such as formatting and styling tools, mail merge functions, and the ability to create automated workflows.
Example: MS Office Integration
When a user creates a chart in Microsoft Excel and wants to insert it into a Microsoft PowerPoint presentation, the user can easily copy and paste the chart from Excel into PowerPoint, or they can use the “Insert” feature in PowerPoint to import the chart directly from Excel. If the user needs to make changes to the data in the chart, they can do so in Excel and the changes will automatically be updated in the chart in PowerPoint. This integration between Excel and PowerPoint, two different components of the Microsoft Office suite, allows for seamless collaboration and efficient workflow.
Productivity Software
Productivity software is a type of software designed to increase productivity and efficiency in completing tasks. It includes tools such as project management software, time tracking software, and collaboration software. Examples of productivity software include:
Trello: a project management tool that uses boards and cards to organize tasks and projects.
Evernote: a note-taking app that allows users to create and organize notes, to-do lists, and reminders.
Asana: a project management tool that helps teams track tasks and progress towards goals.
Slack: a messaging and collaboration app that allows teams to communicate and share files in real-time.
Microsoft Teams: a collaboration platform with messaging, video conferencing, and file sharing capabilities.
Google Drive: a cloud storage and collaboration platform that allows users to create and share documents, spreadsheets, and presentations.
RescueTime: a time-tracking tool that helps users understand how they spend their time on their computer or mobile device.
Grammarly: a writing assistant that checks for spelling and grammar errors, suggests writing improvements, and offers suggestions for clarity and tone.
Zoom: a video conferencing tool that allows users to connect with others remotely for meetings, webinars, and virtual events.
Hootsuite: a social media management tool that allows users to manage multiple social media accounts, schedule posts, and track engagement metrics.
Utilities
Computer utility apps are a type of software designed to optimize the performance and functionality of a computer or electronic device. Examples of computer utility apps include:
Antivirus and malware software: These apps are designed to detect and remove viruses, malware, and other malicious software from a computer or device.
Disk cleanup and optimization: These apps are used to free up space on a computer’s hard drive by deleting unnecessary files and optimizing system performance.
Backup and recovery: These apps are used to back up important files and data to prevent loss in case of a system failure, and to recover data if a system failure does occur.
System maintenance: These apps are used to perform routine maintenance tasks on a computer, such as updating software, scanning for errors, and optimizing performance.
File compression and extraction: These apps are used to compress large files for easier storage and transfer, and to extract files from compressed archives.
Disk defragmentation: This app is used to optimize a computer’s hard drive by rearranging fragmented files and improving system performance.
So, computer utility apps are used to maintain and optimize the performance and functionality of a computer or electronic device, ensuring that it operates smoothly and efficiently.
Enterprise Systems
Enterprise information systems (EIS) are integrated software solutions designed to support and automate various business functions and processes within an organization. These systems help organizations manage and analyze vast amounts of data to make informed decisions and improve overall efficiency. There are several types of enterprise information systems, each specialized for different aspects of business operations.
Enterprise Resource Planning (ERP) Systems: ERP systems integrate core business processes, such as finance, accounting, inventory management, human resources, and supply chain management. They provide a centralized database and real-time visibility into all facets of the organization. Examples of popular ERP systems include SAP, Oracle ERP, and Microsoft Dynamics 365.
Customer Relationship Management (CRM) Systems: CRM systems streamline customer interactions, sales, and marketing processes. They help organizations manage customer data, track leads, and improve customer satisfaction and loyalty. Popular CRM systems include Salesforce, Microsoft Dynamics CRM, and HubSpot.
Supply Chain Management (SCM) Systems: SCM systems optimize the flow of materials, information, and finances involved in the supply chain. They enable organizations to plan, execute, and control the entire supply chain, from procurement to product delivery. Examples of SCM systems are SAP SCM, Oracle SCM, and JDA Software.
Human Resources Management Systems (HRMS): HRMS systems automate HR processes, including recruitment, employee onboarding, payroll management, benefits administration, performance evaluation, and training. They centralize employee data and streamline HR operations. Examples of HRMS systems include Workday, Oracle HCM Cloud, and ADP.
Business Intelligence (BI) Systems: BI systems collect, analyze, and present data from various sources to provide actionable insights and support decision-making. They include tools for data visualization, reporting, and advanced analytics. Examples of popular BI systems are Tableau, Microsoft Power BI, and Qlik.
Knowledge Management (KM) Systems: KM systems capture, store, and share organizational knowledge and information. They facilitate collaboration, knowledge discovery, and knowledge sharing. Examples of KM systems include Microsoft SharePoint, Confluence, and IBM Knowledge Center.
Enterprise Content Management (ECM) Systems: ECM systems manage the creation, storage, retrieval, and distribution of an organization’s documents and content. They ensure document security, compliance, and improve collaboration. Examples of ECM systems are OpenText Content Suite, Microsoft SharePoint, and IBM FileNet.
These enterprise information systems work together to provide a comprehensive view of an organization’s operations and facilitate effective decision-making. By integrating various business functions and processes, EIS enable organizations to streamline their operations, reduce manual work, and improve overall efficiency. We will explore these systems in greater detail later in the text.
Mobile Applications
Mobile applications, or mobile apps, are software applications that are designed to be used on mobile devices such as smartphones and tablets. Mobile apps can be downloaded and installed from app stores such as the Apple App Store and Google Play Store. Mobile apps have become popular due to their convenience and accessibility, as they allow users to access information and perform tasks on the go.
Some examples of popular mobile applications for business include:
Slack: A messaging and collaboration app designed for teams to communicate and share files in real-time.
Trello: A project management app that allows teams to organize and prioritize tasks and projects.
Salesforce: A CRM app that allows sales teams to manage customer relationships and track sales leads on the go.
Dropbox: A file-sharing app that allows users to access and share files from anywhere.
LinkedIn: A professional networking app that allows users to connect with colleagues, find job opportunities, and share industry news.
Mobile apps provide businesses with increased flexibility and productivity, allowing employees to stay connected and productive even when they are on the go.
Cloud Computing

Cloud computing is a type of computing where resources and services are accessed over the internet. This includes servers, storage, and applications, which are provided by third-party providers and hosted on remote servers. Cloud computing allows users to access computing resources and services from anywhere with an internet connection, and it has become increasingly popular in recent years due to its flexibility and cost-effectiveness.
Advantages of cloud computing:
Cost-Effective: Cloud computing eliminates the need for businesses to invest in expensive on-premises hardware and software, reducing upfront costs.
Scalability: Cloud computing allows for easy and quick scalability, meaning businesses can easily increase or decrease the resources they need based on demand.
Accessibility: Cloud computing allows for remote access, allowing users to access computing resources and applications from anywhere with an internet connection.
Disaster Recovery: Cloud computing providers typically have robust disaster recovery measures in place, ensuring that data and applications are backed up and protected in the event of a disaster.
Potential Disadvantages of cloud computing:
Security Concerns: Cloud computing hosts data and applications on remote servers, which can lead to security concerns if proper security measures are not in place.
Dependence on Internet Connection: Cloud computing relies on a stable and reliable internet connection, which can be a limitation for businesses in areas with poor internet connectivity.
Limited Control: Cloud computing providers control and manage the cloud infrastructure, meaning businesses have limited control over their data and applications.
Provider Dependence: Businesses rely on cloud computing providers to maintain and manage the cloud infrastructure, which can be a concern if the provider experiences downtime or other issues.
Virtualization
Virtualization is a technology that enables multiple operating systems to run on a single physical machine, by creating virtual versions of the computing resources such as the CPU, memory, and storage. Virtualization makes it possible to run multiple applications and operating systems on a single physical server, which can lead to increased efficiency and cost savings.
In business, virtualization is used to consolidate multiple physical servers into a single physical machine, which can reduce hardware costs and improve resource utilization. Virtualization also allows for better management and flexibility of computing resources, as virtual machines can be easily created, moved, and deleted as needed.
Advantages of virtualization include:
Cost savings: Virtualization can reduce hardware and maintenance costs by consolidating multiple physical servers into a single machine.
Improved efficiency: Virtualization can improve resource utilization and reduce downtime by allowing virtual machines to be easily moved and managed.
Flexibility: Virtualization allows for easy creation and deployment of virtual machines, making it easier to scale resources up or down as needed.
Disadvantages of virtualization include:
Increased complexity: Virtualization adds an additional layer of complexity to the IT infrastructure, which can make it more difficult to manage and troubleshoot.
Performance issues: Running multiple virtual machines on a single physical machine can lead to performance issues if resources are not properly allocated or if the physical machine is not powerful enough.
Security concerns: Virtualization can create new security vulnerabilities if virtual machines are not properly isolated or if there are vulnerabilities in the virtualization software.
Open-Source Software
Open-source software is software that is distributed with its source code, allowing anyone to access, modify, and distribute the code. This is in contrast to proprietary software, where the source code is kept secret and can only be modified and distributed by the software vendor.
Open-source software is used in business for a variety of purposes, including server management, software development, content management, and collaboration. It can help to reduce costs, increase flexibility and customization, and improve security and reliability.
Some popular examples of open-source software include the Linux operating system, the Apache web server, the MySQL database management system, the WordPress content management system, and the Git version control system.
The pros of open-source software include increased flexibility and customization, reduced costs, improved security and reliability, and a global community of developers contributing to the code. The cons of open-source software include potential compatibility issues, lack of support, and the need for technical expertise to manage and modify the code.
Ultimately, the choice between open-source office software and Microsoft Office depends on the specific needs and preferences of the user. Those looking for a cost-effective option with basic office capabilities may prefer open-source software, while larger organizations or those requiring more advanced features may opt for Microsoft Office.
Microsoft Office vs. OpenOffice
When comparing OpenOffice open-source software with Microsoft Office, there are several key differences to consider.
Cost: Open source office software, such as LibreOffice and OpenOffice, is generally free to use, while Microsoft Office requires a subscription or one-time purchase.
Features: While both options provide word processing, spreadsheet, and presentation capabilities, Microsoft Office may offer more advanced features and integrations with other Microsoft products.
Compatibility: Microsoft Office is the industry standard for office software, meaning that files created in Microsoft Office may not always be fully compatible with open-source office software, and vice versa.
Support: Microsoft Office has a dedicated support team and a large user base, while open-source office software may have limited support options and documentation.
Community: Open-source office software has a global community of developers contributing to the code, while Microsoft Office is proprietary software controlled by Microsoft.
Software Programming
Programming software involves the process of designing, coding, testing, and maintaining software applications. It requires knowledge of programming languages, software development tools, and principles of software engineering.
The software development process typically involves the following stages:
- Requirements gathering: Identifying the needs and requirements of the software application through collaboration with stakeholders and end-users.
- Design: Creating a detailed plan and design for the software, including architecture, user interface, and functionality.
- Implementation: Writing the actual code for the software application using programming languages and software development tools.
- Testing: Testing the software application for bugs, errors, and performance issues.
- Deployment: Launching the software application in production environments.
- Maintenance: Ongoing support and maintenance of the software application, including updates, bug fixes, and enhancements.
Effective software development requires strong teamwork, communication, and project management skills. It involves a continuous cycle of feedback and improvement to ensure that the software application meets the needs of stakeholders and end-users.
What is an Algorithm?
An algorithm is a set of instructions or rules that a computer follows to complete a task or solve a problem.
For example, an algorithm to access a SQL database and move data into a user’s Outlook address book might look like:
- Import software library modules for connecting to the SQL database and interacting with Outlook.
- Establish a connection to the SQL database and retrieve necessary data using SQL queries.
- Iterate through the retrieved data and extract the required fields such as names, phone numbers, and email addresses.
- Create a new Outlook application object.
- Retrieve the contacts folder in Outlook.
- Create a new contact item
- Set the properties of the name, phone number, and email address of the contact item using the appropriate methods and properties.
- Save the contact item using the Save() method.
- Repeat steps 6-8 for all the retrieved data.
- Close the connection to the SQL database and Outlook.
This algorithm would then be used to guide a programmer to select appropriate commands in the programming language they were using to translate the algorithm to something a computer would understand.
Low-Level Programming Languages
Low-level programming languages are programming languages that are closer to the hardware and machine language than high-level programming languages. They are typically used to develop system software, device drivers, and firmware. Examples of low-level programming languages include Assembly language and machine language.
Advantages of using low-level programming languages include:
Better performance: Low-level programming languages can directly access hardware resources, allowing for better performance than high-level programming languages.
Control: Low-level programming languages provide more control over the system hardware, which can be useful for developing system software and device drivers.
Memory efficiency: Low-level programming languages can be memory-efficient since they require less memory to run compared to high-level programming languages.
Disadvantages of using low-level programming languages include:
Steep learning curve: Low-level programming languages can be difficult to learn and require a deep understanding of hardware architecture.
Time-consuming: Developing software in low-level programming languages can be time-consuming since it requires writing more lines of code to accomplish tasks.
Prone to errors: Low-level programming languages are prone to errors such as memory leaks and buffer overflows, which can result in security vulnerabilities.
In the end, the choice of programming language depends on the specific requirements of the project and the expertise of the development team.
Example: Assembly Language
Here is an example of assembly language code in x86 syntax:
; This program calculates the sum of two numbers
section .data
num1 dd 10 ; First number stored in memory location ‘num1’
num2 dd 20 ; Second number stored in memory location ‘num2’
result dd 0 ; Sum of the numbers stored in location ‘result’
section .text
global _start
_start:
mov eax, [num1] ; Load the first number into register ‘eax’
mov ebx, [num2] ; Load the second number into register ‘ebx’
add eax, ebx ; Add the numbers and store the result in ‘eax’
mov [result], eax ; Store the result in location ‘result’
mov eax, 1 ; Prepare to exit with ‘1’ as the return code
xor ebx, ebx ; Clear ‘ebx’
int 0x80 ; Call the kernel to exit the program
; End of program
High-Level Programming Languages
High-level programming languages are programming languages that are designed to be easier to read and write than low-level programming languages. They are typically used to develop application software, such as desktop and mobile applications, web applications, and games. Examples of high-level programming languages include Java, Python, C++, and JavaScript.
Advantages of using high-level programming languages include:
Ease of use: High-level programming languages are designed to be easier to read and write than low-level programming languages, making them more accessible to beginner programmers.
Abstraction: High-level programming languages provide an abstraction from the hardware and machine language, allowing programmers to focus on the functionality of their code rather than the details of the hardware.
Portability: High-level programming languages are typically portable across different operating systems and hardware architectures, making it easier to write software that can run on a variety of devices.
Disadvantages of using high-level programming languages include:
Performance issues: High-level programming languages can be slower than low-level programming languages because they require additional processing time to perform abstractions and translations between the software and the hardware.
Limited control: High-level programming languages provide less control over the hardware than low-level programming languages, which can be a disadvantage for developing system software and device drivers.
Memory inefficiency: High-level programming languages can be memory-inefficient because they require more memory to run compared to low-level programming languages.
Weighing these factors, the choice of programming language depends on the specific requirements of the project and the expertise of the development team. High-level programming languages are typically preferred for developing application software, while low-level programming languages are preferred for developing system software and device drivers.
Example: Python Code
Here is an example of Python code for a simple calculator:
# Simple Calculator Program
“””Function to add two numbers”””
def add(x, y):
return x + y
“””Function to subtract two numbers”””
def subtract(x, y):
return x – y
”””Function to multiply two numbers”””
def multiply(x, y):
return x * y
“””Function to divide two numbers”””
def divide(x, y):
if y == 0:
return “Cannot divide by zero”
else:
return x / y
# Main code
print(“Select operation.”)
print(“1.Add”)
print(“2.Subtract”)
print(“3.Multiply”)
print(“4.Divide”)
choice = input(“Enter choice(1/2/3/4): “)
num1 = float(input(“Enter first number: “))
num2 = float(input(“Enter second number: “))
if choice == ‘1’:
print(num1,”+”,num2,”=”, add(num1,num2))
elif choice == ‘2’:
print(num1,”-“,num2,”=”, subtract(num1,num2))
elif choice == ‘3’:
print(num1,”*”,num2,”=”, multiply(num1,num2))
elif choice == ‘4’:
print(num1,”/”,num2,”=”, divide(num1,num2))
else:
print(“Invalid input”)
Compiled versus Scripted Languages
Compiled code is code that has been translated into machine code by a compiler, resulting in a standalone executable file that can be run directly on a computer without the need for any additional software. In summary, a compiler works by taking source code written in a high-level programming language and translating it into machine code that can be run on a computer. The process involves several stages, including lexical analysis, parsing, semantic analysis, code generation, and optimization. The resulting executable file can be run directly on the computer without the need for any additional software, offering faster execution and better performance compared to scripts.
Script, on the other hand, is code that needs to be interpreted by an interpreter or runtime environment in real-time to be executed. Scripts are usually written in high-level programming languages and require the presence of the interpreter or runtime environment to be executed. Compiled code results in faster execution and better performance, while scripts offer more flexibility and ease of use for developers.
Example: Javascript
// This is a basic JavaScript program that prompts the user for their name and age, and then displays a message with that information
const name = prompt(“What is your name?”);
const age = prompt(“What is your age?”);
alert(Hello ${name}, you are ${age} years old.);
Software Engineering
Software engineering is the process of designing, developing, testing, and maintaining software applications using various engineering principles and practices. It involves programming, project management, and problem-solving skills to create high-quality software that meets the needs of users and stakeholders. Software engineers use various tools and methodologies to ensure that the software is reliable, scalable, and maintainable.
The software engineering process typically involves requirements gathering, design, implementation, testing, deployment, and maintenance. Software engineering is a broad field that covers various specializations, such as web development, mobile app development, and system software development.
Software Engineering for Large Scale Projects
Developing large scale software projects can be challenging due to various factors such as complexity, team size, and coordination. Some of the main challenges include:
Project management: Managing a large team requires proper planning, coordination, and communication. Project managers must ensure that everyone is working towards the same goal and that timelines are being met.
Scaling: As the project grows, it becomes more complex and difficult to manage. Developers must ensure that the system is scalable and can handle large amounts of data and users.
Integration: Large projects often involve integrating multiple systems and technologies. This can be challenging as developers must ensure that all the components work seamlessly together.
Testing: Large projects require extensive testing to ensure that the software is stable and reliable. Testing involves various techniques such as unit testing, integration testing, and user acceptance testing.
To address these challenges, software engineers use various tools and methodologies such as Agile, DevOps, and continuous integration and delivery. These approaches emphasize collaboration, flexibility, and automation to ensure that software projects are delivered on time and within budget.
Additionally, modular design and code can help to simplify the development process and make it easier to manage and integrate different components. Successful development of large scale software projects requires a combination of technical expertise, project management skills, and effective communication and collaboration.
Waterfall versus Agile Software Engineering Approaches
The waterfall method of software development is a linear approach where each stage of the development process is completed in a sequential order. The stages typically include requirements gathering, design, implementation, testing, and deployment. Once a stage is completed, the project moves onto the next stage without any revisiting of the previous stage.
Advantages of the waterfall method include clear goal-setting and defined stages that can be easily tracked and measured. However, the disadvantages include the lack of flexibility for changes or adjustments during the development process, and the risk of potential errors or issues being discovered at a later stage in the process that may require significant rework and delay.
Agile methodology, on the other hand, is an iterative and flexible approach to software development that emphasizes collaboration, customer involvement, and adaptability. Instead of completing each stage before moving on to the next, the agile approach involves ongoing feedback and adjustments throughout the development process.
Advantages of agile methodology include the ability to respond quickly to changes, a focus on customer satisfaction, and increased collaboration and communication among team members. The disadvantages may include a lack of defined goals and timelines, a potential for scope creep, and a need for more frequent updates and assessments.
In light of the advantages and disadvantages of each, the choice of methodology depends on the specific needs and requirements of the project, the development team’s expertise, and the stakeholders’ preferences. Some projects may benefit from a more structured approach like waterfall, while others may require the flexibility and adaptability of agile methodology.
Computer Networking
Computer networking is a field responsible for the creation and maintenance of computer networks, which, in turn, are responsible for the interconnection of devices and systems, allowing the exchange of data and information. In essence, it is the physical and logical infrastructure that links devices, computers, servers, and other devices within a network, enabling them to communicate and access resources that exist in other devices, with the primary goal of enhancing cooperation and the sharing of resources.
A computer network can be made up of two or more devices and could cover a small room or span multiple levels of a building, connecting computers, printers, routers, switches, servers, modems, and other hardware components used to create a working network. But what is the backbone of these networks? In most cases, it’s the Internet.
To understand computer networking it important to start from the basics, and in this case, that means understanding the different types of computer networks. Computer networks come in different types depending on their coverage areas or the nature of information exchanged in them.
Types of Computer Networks
There are several types of computer networks, each with unique features and purposes. These types include LAN, WAN, and VPN and are described below.
Local Area Network (LAN): A LAN is a network that connects devices within a limited geographical area, such as a home or office building. LANs are the most common type of network and are used for sharing data, printers, and internet access among devices. LANs are typically designed to be fast and reliable, with low latency and high bandwidth. Ethernet and Wi-Fi are the most common technologies used to connect devices in a LAN. Equipment needed for a LAN includes Ethernet cables or Wi-Fi routers, switches, network interface cards, and printers. The advantages of a LAN include fast data transfer, low latency, and the ability to share resources among devices. The disadvantages of a LAN include limited geographical coverage and the need for additional equipment such as routers, switches, and cables.
Wide Area Network (WAN): A WAN is a network that connects devices over a large geographical area, such as multiple LANs across different cities or countries. WANs are used for sharing data and resources among devices in different locations. The internet is the most extensive WAN, connecting billions of devices across the world. Equipment needed for a WAN includes routers and switches, leased lines or satellite links, and internet service providers (ISPs). The advantages of a WAN include the ability to connect devices over long distances, access to remote resources, and cost savings. The disadvantages of a WAN include high latency, slow data transfer, and vulnerability to security breaches.
Virtual Private Network (VPN): A VPN is a network that connects devices over the internet, providing a secure and private connection. VPNs are used for accessing remote networks securely, enabling data transfer between devices in different locations. Equipment needed for a VPN includes VPN servers and clients, and secure protocols such as SSL (Secure Sockets Layer) and IPSec (Internet Protocol Security). The advantages of a VPN include secure data transfer, private connection, and remote access. The disadvantages of a VPN include slow data transfer due to encryption and the need for specialized equipment and software.
Networking Equipment: Functions of Routers, Switches, Modems, Hotspots, and Access Points
 Routers. Routers are networking devices that connect LANs or WANs, directing traffic between them. They function as gatekeepers, determining which devices have access to the network and how the traffic flows. Routers use IP addresses to identify devices and use routing tables to determine the best path for data to travel between networks. They also provide security features such as firewalls and VPNs, protecting networks from cyber threats.
Routers. Routers are networking devices that connect LANs or WANs, directing traffic between them. They function as gatekeepers, determining which devices have access to the network and how the traffic flows. Routers use IP addresses to identify devices and use routing tables to determine the best path for data to travel between networks. They also provide security features such as firewalls and VPNs, protecting networks from cyber threats.
Switches. Switches are networking devices that connect devices within a LAN, providing a high-speed connection with low latency. Switches use MAC addresses to identify devices and allow for efficient data transfer between them. They use forwarding tables to direct data to the appropriate device and can be managed or unmanaged. Managed switches offer more control over the network, allowing administrators to configure and monitor network performance.
Modems. Modems are networking devices that connect devices to the internet or other WANs. They convert digital signals from devices into analog signals that can be transmitted over telephone lines or cable connections. Modems use various modulation techniques, such as QAM (Quadrature Amplitude Modulation) and QPSK (Quadrature Phase-Shift Keying), to encode and decode data, allowing for efficient data transfer over long distances.
Hotspots. Hotspots are wireless access points that provide internet access to devices within a limited geographical area, such as a coffee shop or hotel room. Hotspots can be public or private and use various technologies such as Wi-Fi or Bluetooth. They require a wireless router or other networking device to provide internet access.
Access Points. Access points are networking devices that connect devices to a wireless LAN, providing wireless connectivity within a limited geographical area such as a home or office. Access points use various technologies such as Wi-Fi or Bluetooth and allow for efficient data transfer between devices. They are often used in conjunction with routers and switches to create a LAN. Access points can be managed or unmanaged, with managed access points providing more control over the network.
In summary, routers, switches, modems, hotspots, and access points are essential networking devices that enable efficient data transfer between devices within a LAN or WAN. They provide connectivity, security, and control over the network, allowing for seamless communication and collaboration between devices. As technology continues to evolve, the importance of these devices in supporting computer networking will only continue to grow.
Network Software
To create a network, various software and tools are required, depending on the type and size of the network. Some examples of software used to create a network include:
Network Operating System (NOS): This software is used to manage and control the network. It provides various services such as file sharing, print sharing, and user authentication. Examples of NOS include Windows Server, Linux, and Unix.
Network Configuration Tools: These tools are used to configure network settings such as IP addresses, subnet masks, and DNS servers. Some examples of network configuration tools include Cisco Network Assistant, SolarWinds Network Configuration Manager, and NetSetMan.
Network Monitoring and Analysis Tools: These tools are used to monitor network performance, analyze network traffic, and troubleshoot network issues. Examples of network monitoring and analysis tools include Wireshark, Nagios, and PRTG Network Monitor.
Virtual Private Network (VPN) Software: This software is used to create secure connections between remote devices and networks, allowing users to access resources on the network securely. Examples of VPN software include OpenVPN, NordVPN, and ExpressVPN.
Firewall Software: This software is used to protect the network from unauthorized access and other security threats. Examples of firewall software include Windows Firewall, Norton Security, and McAfee Firewall.
Together, these software and tools are essential components in creating and maintaining a network. They provide the necessary functionality to manage, configure, monitor, and protect the network, ensuring that it is secure, efficient, and reliable.
Network Security
Network security refers to the protection of a network and its components from unauthorized access, theft, and damage. Network security concerns can include data breaches, malware, unauthorized access, denial-of-service attacks, and insider threats. These security concerns can lead to the theft of sensitive information, operational disruption, reputational damage, and financial losses. Therefore, it is crucial to protect a network against these security concerns to ensure that it remains secure and operational.
Here are some ways in which we can protect networks against security concerns:
Implement Strong Passwords and Authentication: Weak passwords are a common cause of security breaches. Passwords should be complex, unique, and changed regularly. Implementing multi-factor authentication adds an additional layer of security by requiring a second form of verification, such as a fingerprint or code.
Install Security Software: Anti-virus and anti-malware software can protect against the most common security threats. Firewall software can prevent unauthorized access and detect suspicious activities. Intrusion detection and prevention systems can monitor the network and alert administrators of potential attacks.
Regularly Update Software and Hardware: Software and hardware manufacturers regularly release updates to fix security vulnerabilities. It is essential to keep all devices and software up-to-date to ensure that the network remains secure.
Conduct Regular Security Audits: Conducting regular security audits can help identify vulnerabilities and areas that need improvement. These audits can help to identify gaps in security and make improvements to prevent potential security breaches.
Educate Employees: Employees are often the weakest link in network security. Implementing training programs can help employees understand the importance of network security and how to identify and prevent security breaches.
Physical Security: Physical security measures can prevent unauthorized access to network components. Server rooms and data centers should be locked and secured, and only authorized personnel should have access.
In conclusion, network security is essential in today’s digital age. Protecting a network from security concerns requires an understanding of the risks and implementing appropriate security measures. By implementing strong passwords and authentication, security software, regular updates, security audits, employee education, and physical security measures, a network can be protected from potential security breaches. As technology continues to advance, it is crucial to remain vigilant and adapt to new security threats to ensure that networks remain secure and operational.
The Internet and World Wide Web
The Internet is a global network of computer networks that enables the exchange of information and resources between millions of devices worldwide. The history of the Internet dates back to the 1960s when the US Department of Defense’s Advanced Research Project Agency (ARPA) developed a packet-switching system called ARPANET. The primary purpose of ARPANET was to share information between military and academic institutions. In 1983, ARPANET switched from the Network Control Protocol (NCP) to the Transmission Control Protocol/Internet Protocol (TCP/IP), which formed the foundation of the modern internet.
 The World Wide Web (WWW), often referred to simply as the ‘web,’ is an information system that allows documents to be linked and accessed over the internet. The web was invented by British computer scientist Tim Berners-Lee in 1989 while working at CERN (European Organization for Nuclear Research) in Switzerland. Berners-Lee developed the Hypertext Transfer Protocol (HTTP) and the HyperText Markup Language (HTML) that form the basis of the web. In 1993, the first web browser, Mosaic, was released, which allowed users to access web pages with ease.
The World Wide Web (WWW), often referred to simply as the ‘web,’ is an information system that allows documents to be linked and accessed over the internet. The web was invented by British computer scientist Tim Berners-Lee in 1989 while working at CERN (European Organization for Nuclear Research) in Switzerland. Berners-Lee developed the Hypertext Transfer Protocol (HTTP) and the HyperText Markup Language (HTML) that form the basis of the web. In 1993, the first web browser, Mosaic, was released, which allowed users to access web pages with ease.
The web quickly grew in popularity, and by the mid-1990s, it had become a global phenomenon. The web provided a platform for individuals and businesses to share information and communicate with each other, transforming the way we live and work. Today, the web is an essential tool for businesses, governments, and individuals, and it has become an integral part of our daily lives.
The Importance of the Internet to Business Today
The internet has had a significant impact on businesses worldwide, providing them with opportunities for growth and expansion. Here are some reasons why the internet is essential to businesses today:
Global Reach. The internet provides businesses with the ability to reach customers and clients worldwide, breaking down geographical barriers. Companies can now market their products and services to a global audience through their website, social media, email marketing, and online advertising.
E-commerce. The rise of e-commerce has revolutionized the way businesses sell products and services. Companies can now set up online stores and sell their products directly to customers, cutting out the middleman. E-commerce has enabled small businesses to compete with big corporations, providing them with a platform to reach a global audience.
Communication. The internet has transformed the way businesses communicate with each other, their employees, and their customers. Email, instant messaging, video conferencing, and other messaging apps have made it easier for businesses to communicate with employees and customers in different locations. This has increased efficiency and productivity, reduced costs associated with travel, and improved customer service.
Data Analysis. The internet has also provided businesses with access to vast amounts of data that can be used to improve their operations. Big data analytics tools can be used to extract insights from this data, enabling businesses to make informed decisions and improve their operations. This has led to the development of new business models and the creation of innovative products and services.
In conclusion, the internet has transformed the way businesses operate, providing them with opportunities for growth and expansion. It has enabled businesses to reach a global audience, sell products and services online, improve communication, and make data-driven decisions. As technology continues to evolve, the importance of the internet to businesses will only continue to grow. Businesses that embrace the internet and stay up-to-date with the latest trends and technologies will have a significant advantage over their competitors.
Internet of Things
 The internet of things (IoT) refers to the network of interconnected physical devices and objects that are embedded with sensors and software, allowing them to collect and exchange data over the internet. This includes anything from smart home appliances and wearables to industrial sensors and autonomous vehicles.
The internet of things (IoT) refers to the network of interconnected physical devices and objects that are embedded with sensors and software, allowing them to collect and exchange data over the internet. This includes anything from smart home appliances and wearables to industrial sensors and autonomous vehicles.
The concept of IoT has been around since the 1990s, but it has only become practical in recent years with the development of affordable and reliable sensors, wireless connectivity, and cloud computing. The importance of IoT lies in its potential to revolutionize the way we live and work by enabling greater automation, efficiency, and data-driven decision-making. For example, smart homes can adjust lighting and temperature based on user preferences, while factories can optimize production processes and reduce waste through real-time monitoring and analytics. However, IoT also raises concerns around privacy, security, and data ownership, as the vast amounts of data generated by IoT devices can be sensitive and personal.
Summary
The chapter begins by highlighting the importance of computer hardware. Computers have become an integral part of our daily lives, and businesses rely heavily on them for their operations. They are used for everything from storing data and information to connecting with clients and colleagues. The chapter goes on to discuss the key components of computer hardware, including CPUs, RAM, and storage devices. It highlights the importance of choosing the right hardware for different business needs.
Software is also a critical element of modern business operations. The chapter emphasizes that the right software can help businesses operate more efficiently and increase their productivity. The chapter discusses the different types of software used in business, including applications for individuals and the enterprise.
Networking is another important element of business technology. Networking allows businesses to connect with clients and colleagues around the world, and it enables employees to work remotely. The chapter discusses the different types of networks used in business, including LANs, WANs, and the internet. The internet has revolutionized the way that businesses operate, allowing them to reach customers around the world and conduct transactions online.
This chapter emphasizes the crucial role that technology plays in modern business operations. It highlights the importance of staying up-to-date with the latest hardware, software, and networking tools.
Discussion Questions:
- How do different hardware components work together to form a computer system?
- What are the advantages and disadvantages of proprietary versus open-source software?
- What are the key principles of networking and how do they apply to business environments?
- How has the internet revolutionized business communication and marketing strategies?
- What are the ethical implications of collecting, storing, and analyzing user data on the internet?
- How can businesses utilize cloud computing to improve their operations and reduce costs?
- What are the key security risks that businesses face in terms of hardware, software, and network security?
- How can big data analytics be used to drive business decisions and improve performance?
- What emerging technologies or trends in hardware, software, and networking will have the greatest impact on business in the next decade?

